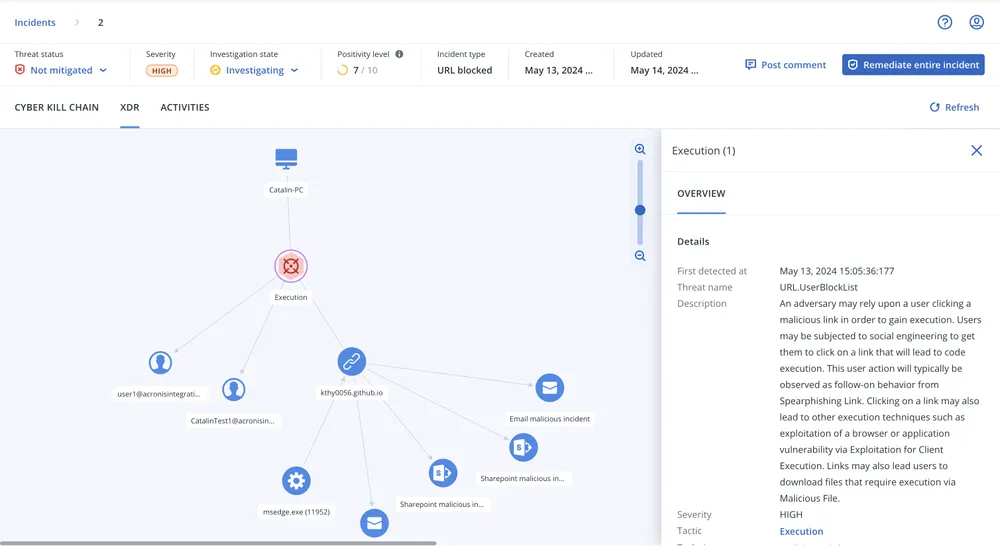
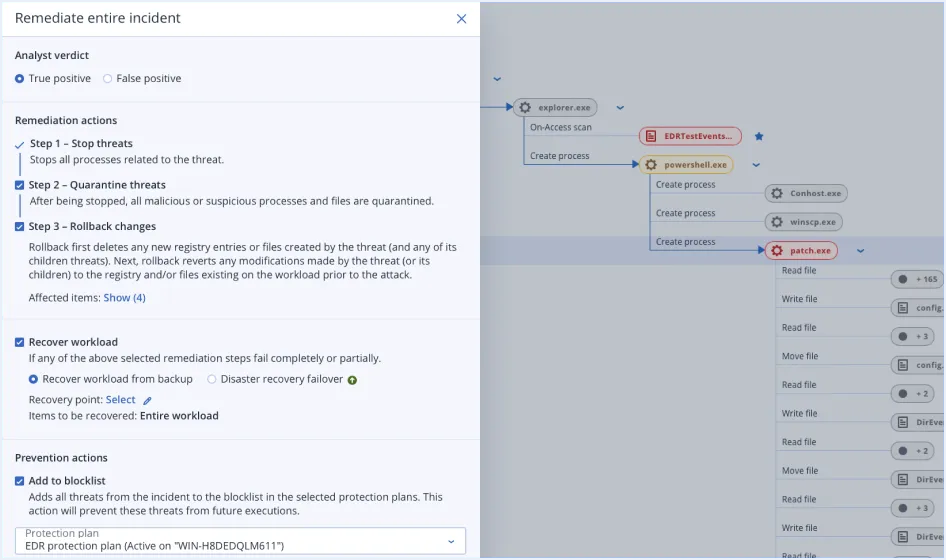
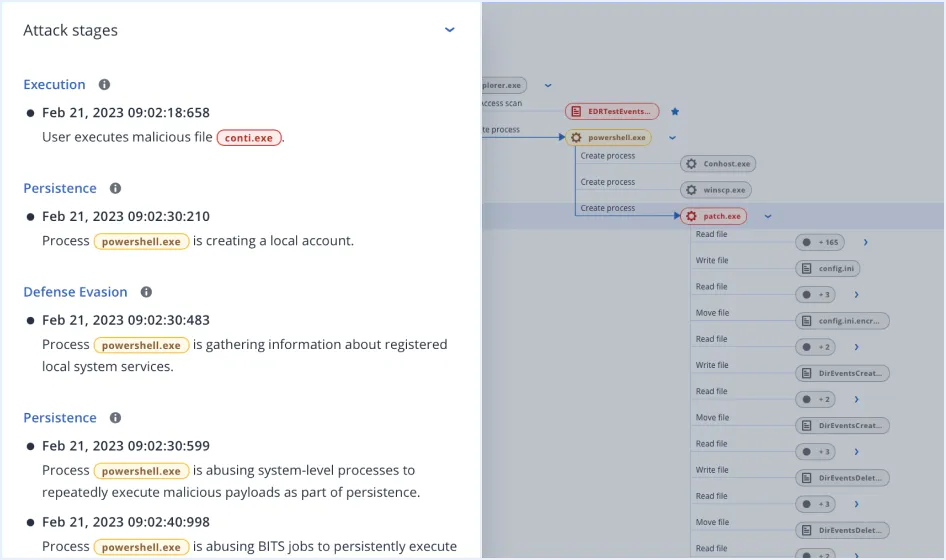
XDR (Extended Detection and Response) is an advanced cybersecurity solution that unifies data from endpoints, email, identity, and networks. Using AI-driven insights, it enhances visibility, correlates events, and enables rapid, context-rich threat detection and response.