| Behavior-based detection | | | |
| Vulnerability assessments | | | |
| Device control | | | |
| File- and system-level backup | | | |
| Inventory collection (with Advanced Management) | | | |
| Patch management (with Advanced Management) | | | |
| URL filtering | | | |
| Exploit prevention | | | |
| Real-time threat intelligence feed | | | |
| Threat hunting – Early access | | | |
| Automated, tunable allowlisting based on profiling | | | |
| Forensic data collection | | | |
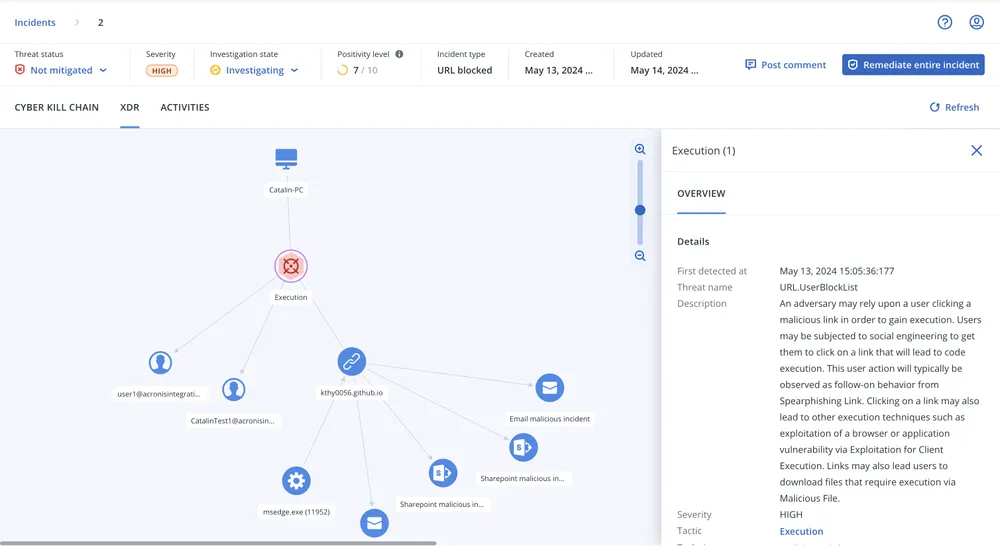
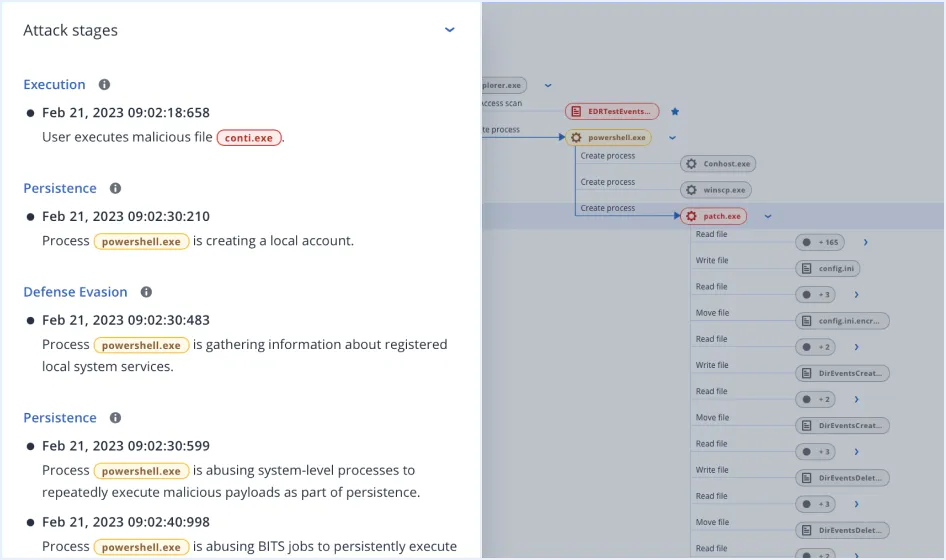
| Event monitoring | | | |
| Automated event correlation | | | |
| GenAI assistant (Acronis Copilot – Early Access) | | | |
| Prioritization of suspicious activities | | | |
| AI-generated incident summaries | | | |
| Automated MITRE ATT&CK® attack chain visualization and interpretation | | | |
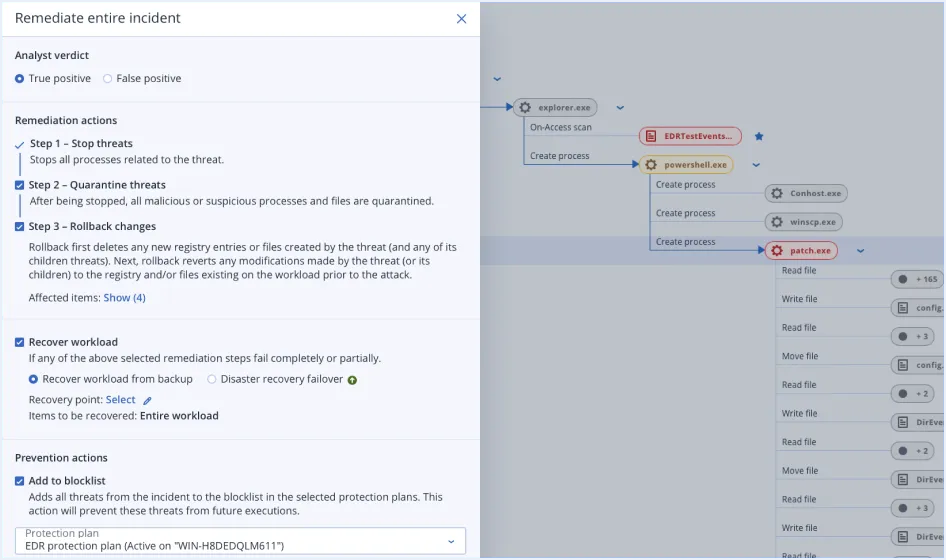
| Single-click response to incidents | | | |
| Full threat containment including endpoint quarantine and isolation | | | |
| Automated response playbooks | | | |
| Intelligent search for IoCs including emerging threats | | | |
| Attack-specific rollback | | | |
| Anti-ransomware protection with automatic rollback | | | |
| Integration with Microsoft 365 apps (SharePoint, OneDrive, Teams, and Outlook, Entra ID) | | | |
| Integration with Advanced Email Security (email telemetry) | | | |
| Integration with Collaboration App Security (Microsoft 365 apps telemetry) | | | |
| Delete malicious email attachment or URLs | | | |
| Search for malicious attachments across mailboxes | | | |
| Block malicious email address | | | |
| Terminate all user sessions | | | |
| Force user account password reset on next login | | | |
| Suspend user account | | | |
| MDR service | | | |
| Public API for EDR | | | |