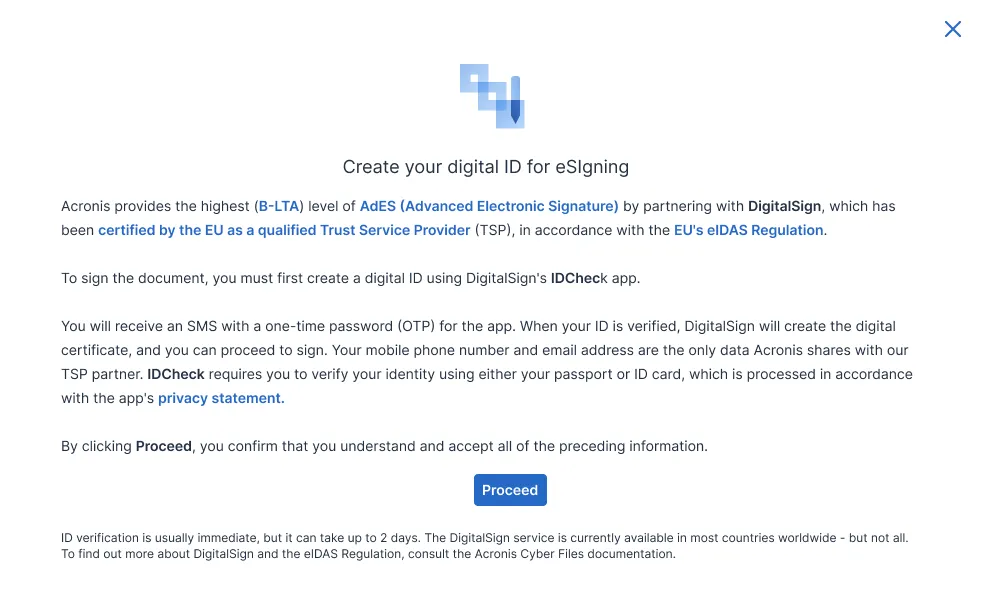
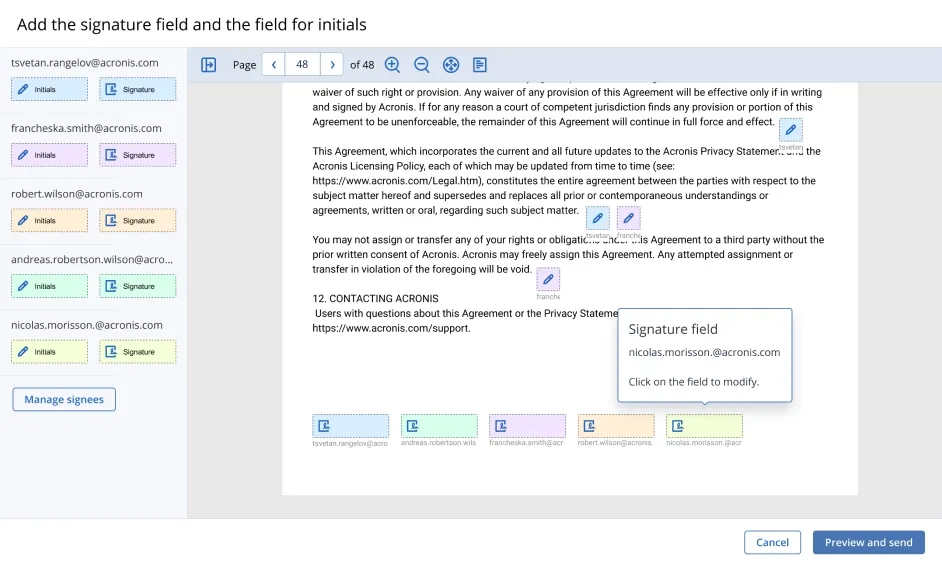
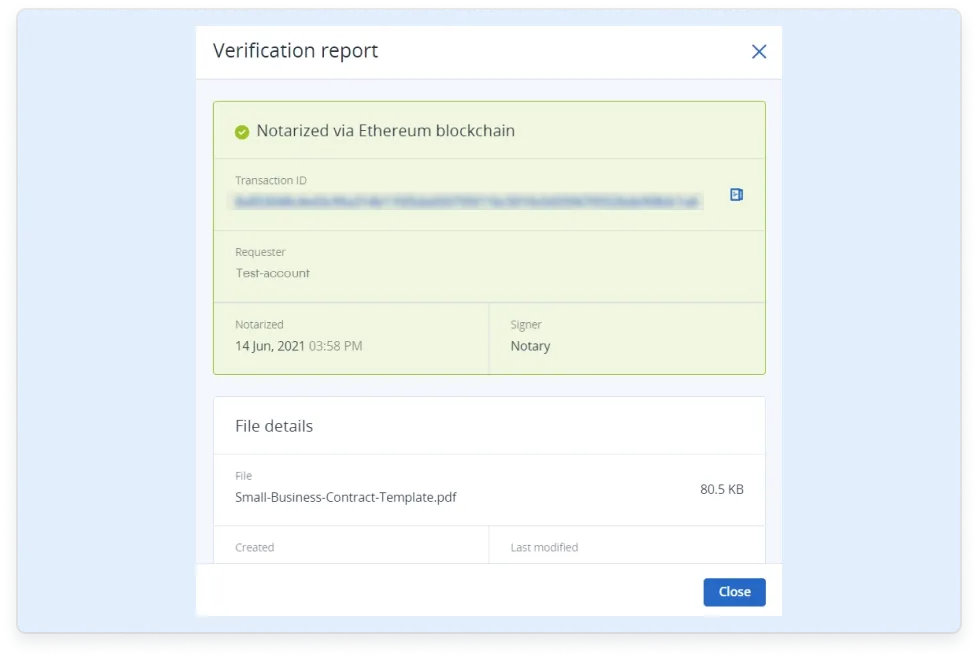
eIDAS is a European Union regulation, formally known as the Electronic Identification and Trust Services Regulation (Regulation 910/2014/EC).
In the past, contracts were typically expected to be signed in person with a traditional wet-ink signature. The eIDAS regulation enables businesses and customers to sign contracts digitally and securely, opening the door to faster, safer, and more efficient cross-border transactions.