
on the market
users worldwide
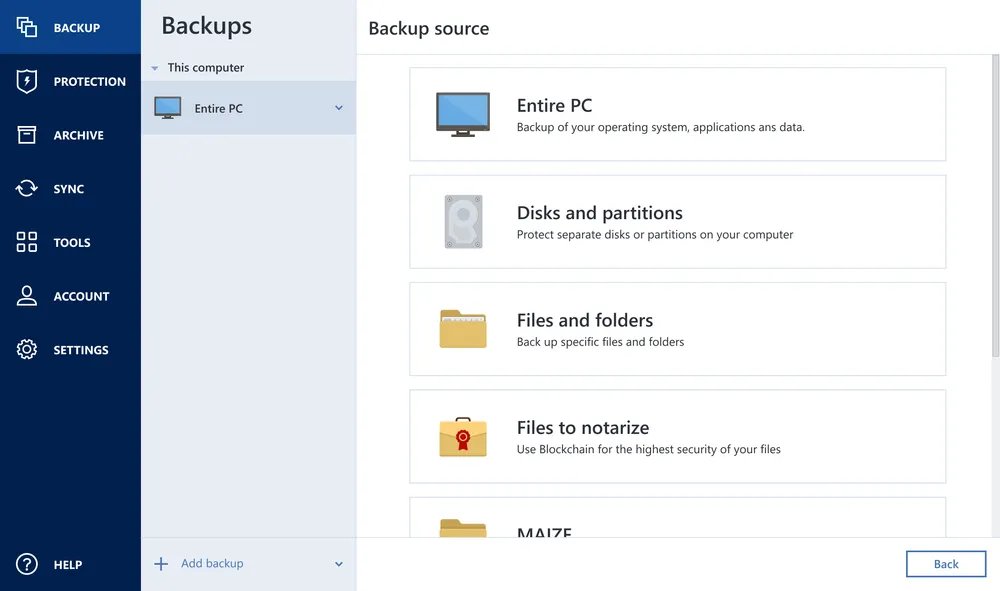
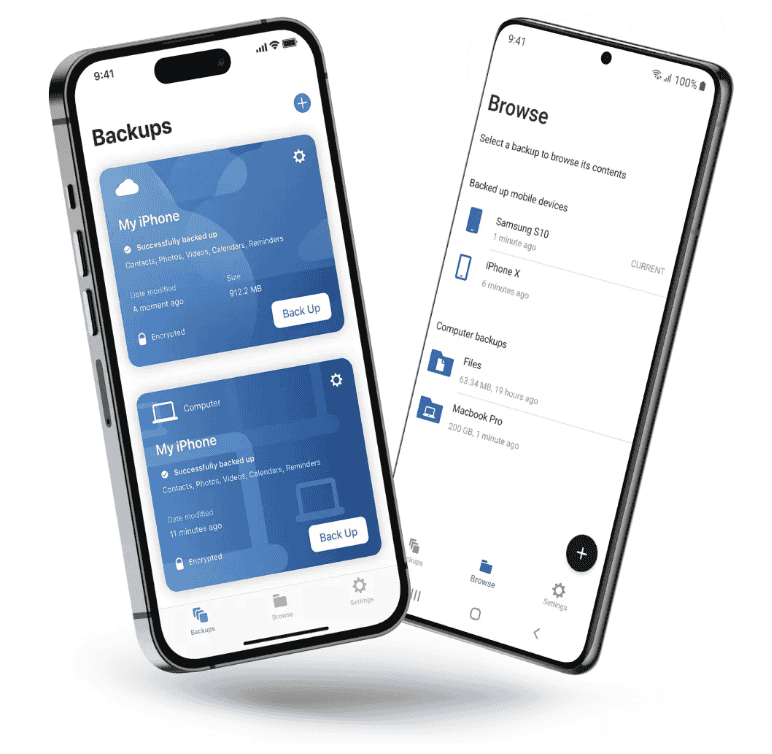
backups and clones
cyberattacks prevented last year
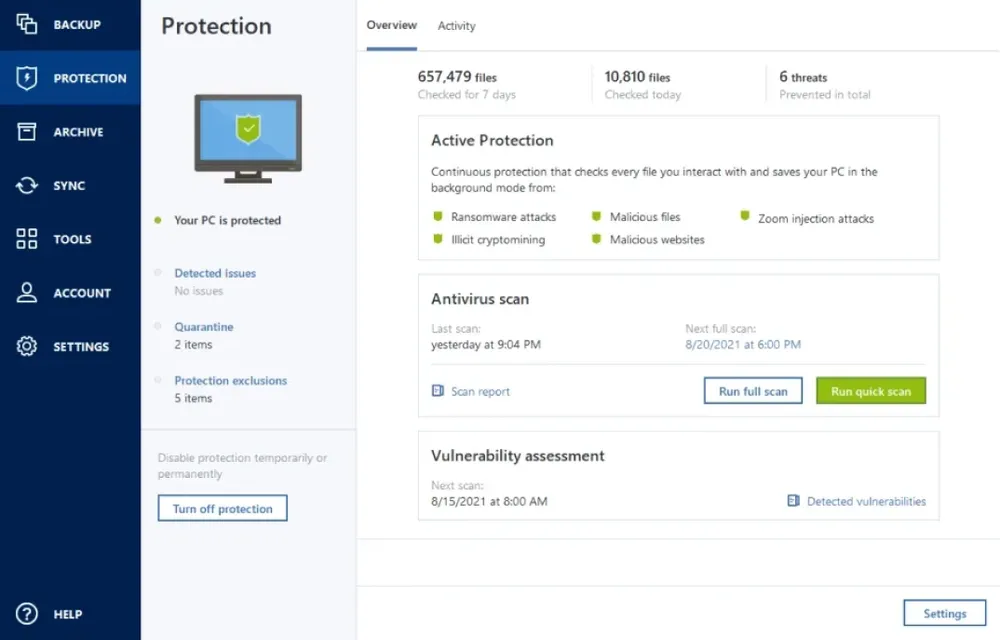
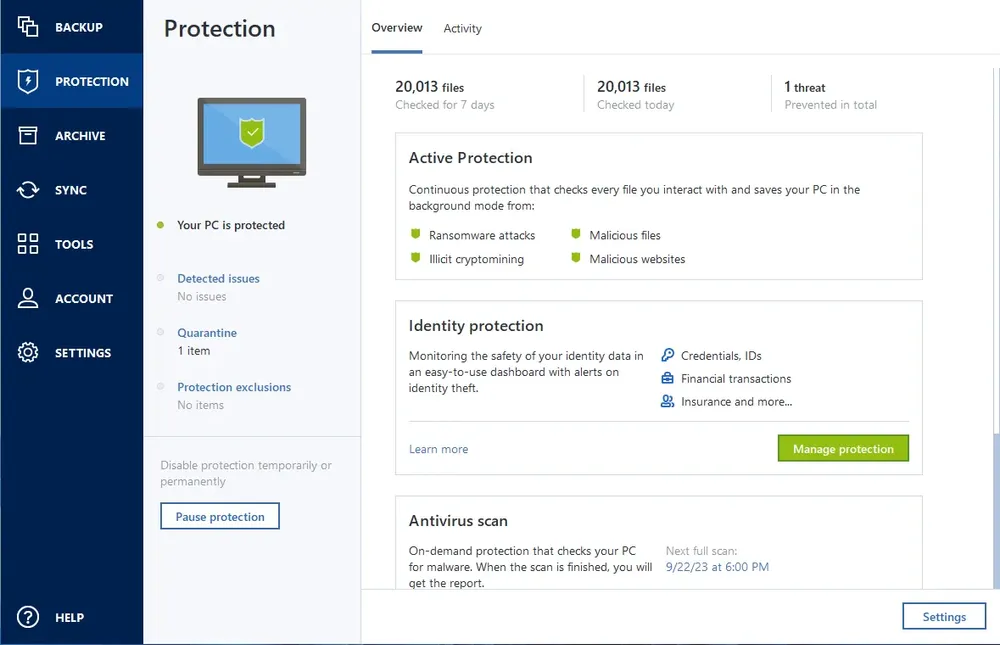
Be protected from the unexpected. The complete cybersecurity protection you need with an easy-to-use and reliable solution against data loss, cyberattacks, and identity theft.*



• Time-proven technology
• Millions of satisfied users
• Complete control of the backup process
• Fast backup and recovery
• Fast upload and download of data
• Pre-configured full-system backup plan
• Intuitive user interface
• One-click backup
• Automatic protection
• Windows
• macOS
• iPhones and iPads
• Android phones and
tablets
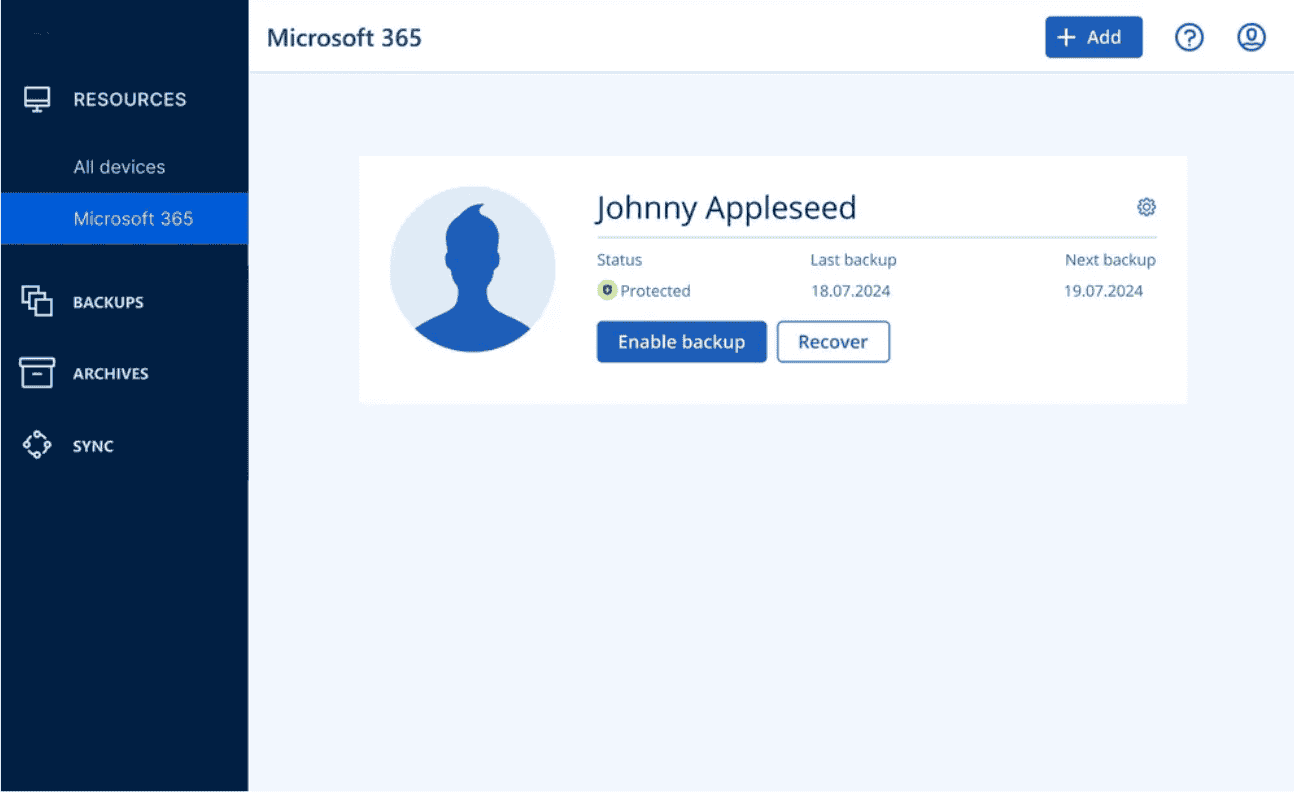
• Outlook mailboxes
• OneDrive
Formerly Acronis Cyber Protect Home Office
Local backup & Anti-ransomware protection
One-year subscription
Local and сloud backup & Security
One-year subscription
Local backup & Anti-ransomware protection
One-year subscription
Over 5.5 million users rely on Acronis True Image every day






Securing multi-site and industrial IT against IT complexity, spiraling costs and downtime.

Vulnerability assessments, patch management and removal of malware from backups.

Continuous data protection, AI and ML-based real-time protection against malware including ransomware and zero-day threats.
Rapid recovery of data, integrated disaster recovery and user-initiated, one-click recovery, including bare-metal recovery.
Discover how Cyber Protect expedites recovery, secures backups, slashes TCO, and fortifies multi-site IT and industrial computing against modern cyber threats.
Windows 7 SP1 (all editions)
ReiserFS(3)
Linux SWAP
HFS+/HFSX
FAT16/32/exFAT
Keep your mobile contacts, calendars, photos and files safe. Our free Acronis mobile app safeguards your device, as well as all of your family’s smartphones and tablets with Acronis True Image (formerly Acronis Cyber Protect Home Office).
Acronis Cyber Protect v16 delivers swift user-driven recovery of any computing system, regardless of age or function, crucial in minimizing operational disruptions. It uniquely delivers:
• Recovery of any computer regardless of age or function: Capable of recovering any systems, old or new, v16 ensures dependable and swift recovery. This is inclusive of a bare-metal restore to new hardware, essential for sustaining continuity with aging legacy systems.
• User-Driven Recovery: With One-Click Recovery, non-technical personnel can easily initiate recovery processes, effectively decentralizing IT workload and accelerating the return to operation, post-incident.
• Industry-Specific Recovery: Acronis v16 is tailored for the unique needs of industrial environments, offering targeted recovery for OT, ICS, and laboratory systems. This mitigates downtime risks in sectors where every second of production time is valuable.
• Compatibility Assurance: Cyber Protect boasts verified compatibility with all major OT and ICS providers, ensuring seamless integration and reliability.
• Self-service remote recovery: Remote and home office users can independently recover systems, vastly improving recovery time objectives (RTO) across diverse locations without central IT intervention.
Acronis Cyber Protect v16 is all about getting systems back online fast, without needing a lot of technical help, which is great for busy industrial settings.
Acronis Cyber Protect v16 helps reduce the total cost of ownership (TCO) for cyber protection solutions through several key features:
• Comprehensive Workload Support: With support for over 20 different workloads, including on-premises, cloud, and SaaS platforms, Acronis Cyber Protect v16 allows enterprises to streamline their data protection efforts across diverse IT environments. This extensive support facilitates vendor consolidation, simplifying management, and ensuring that all aspects of the enterprise IT infrastructure are comprehensively protected.
• Streamlined Management: The centralized management console simplifies the oversight of data protection and cybersecurity across the enterprise, thereby saving administrative time and reducing operational costs.• One-click Recovery: The one-click recovery feature empowers users to restore systems independently, reducing the burden on IT staff and minimizing downtime, which can be costly for businesses.
• Automated Processes: With automated features like patch management and vulnerability assessments, routine tasks are handled efficiently, allowing IT teams to focus on more strategic initiatives rather than time-consuming maintenance.
• Resource Efficiency: Acronis Cyber Protect v16 is designed to minimize the impact on system resources, ensuring that protection operations don’t interfere with productivity and do not require additional investment in hardware.
• Proactive Protection: Advanced AI and ML technologies help prevent cyber incidents before they occur, reducing the potential costs associated with data breaches, ransomware recovery, and system remediation.
• Compatibility with Legacy Systems: The ability to support and recover older systems with bare-metal recovery means that organizations can extend the life of their existing infrastructure without incurring costs for immediate upgrades.
• Data Sovereignty and Compliance: The built-in compliance and data sovereignty features help avoid fines and penalties associated with non-compliance, which can add up significantly for enterprises operating in multiple jurisdictions.
By focusing on these areas, Acronis Cyber Protect v16 allows enterprises to manage cyber protection more efficiently, both operationally and financially, leading to a lower TCO.
The auto-discovery feature in Acronis Cyber Protect v16 significantly simplifies the process of safeguarding new devices within an enterprise network. This is particularly useful for multi-site environments and remote IT. Here’s how it enhances the protection workflow:
• Automatic Device Detection: As soon as a new device connects to the network, Acronis Cyber Protect v16’s auto-discovery tool automatically detects it. This eliminates the need for manual monitoring and inventorying of new hardware additions, ensuring no device goes unprotected due to oversight or the lag of manual processes.
• Seamless Integration: Once a new device is detected, the system can be configured to automatically deploy the Acronis agent. This means that the device is immediately brought under the protection umbrella of Acronis Cyber Protect without any manual intervention, ensuring rapid defense against potential threats.
• Consistent Policy Application: With auto-discovery, the protection policies predefined for the enterprise are automatically applied to the new devices. This ensures that each device adheres to the company’s cybersecurity standards, maintaining consistency and compliance across the entire network.
• Efficient Resource Allocation: By automating the initial steps of device protection, IT teams are relieved of repetitive tasks, allowing them to focus on more strategic initiatives. This efficient use of human resources contributes to a reduction in operational costs and enhances overall productivity.
In essence, Acronis Cyber Protect v16’s auto-discovery feature streamlines the expansion of network protection, ensures immediate and consistent security coverage for new devices, and optimizes IT resource utilization.
Acronis Cloud Storage is a storage option that saves backups to safe and secure Acronis Data Centers. Acronis Cloud Storage licenses are subscription-based and depend on the storage capacity levels. You can save backups from an unlimited number of machines and any type of platform to cloud storage, including mobile device backups. The quota is shared among all the devices registered in the account*.
(!) Note that to use Acronis Cloud Storage you need at least one Acronis Cyber Protect license.
*Does not apply to the free cloud storage. The free cloud storage available with a subscription license is valid only for the licensed workload and cannot be shared across other workloads.