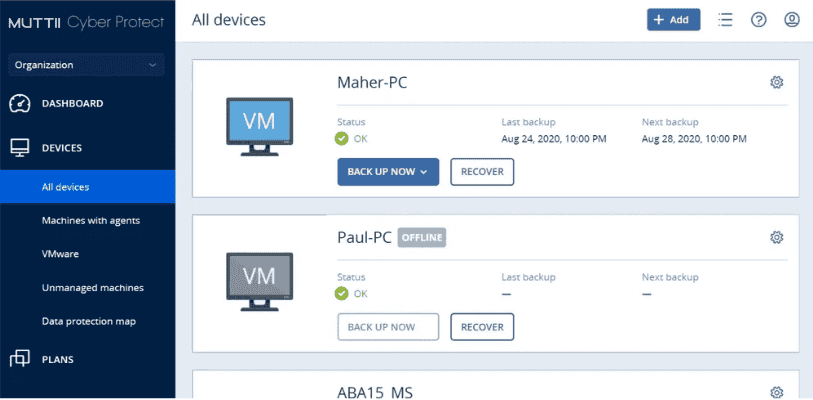
Deliver the most secure backup and fastest recovery for multi-site, multi-generational and industrial IT. Restore any system without IT intervention, while cutting TCO and simplifying management for maximum efficiency and resilience.



Deliver AI-powered protection against cyber threats
Empower users with self-service recovery.
Reduce TCO through vendor consolidation
Simplify management with a single unified console
Address data sovereignty challenges effectively
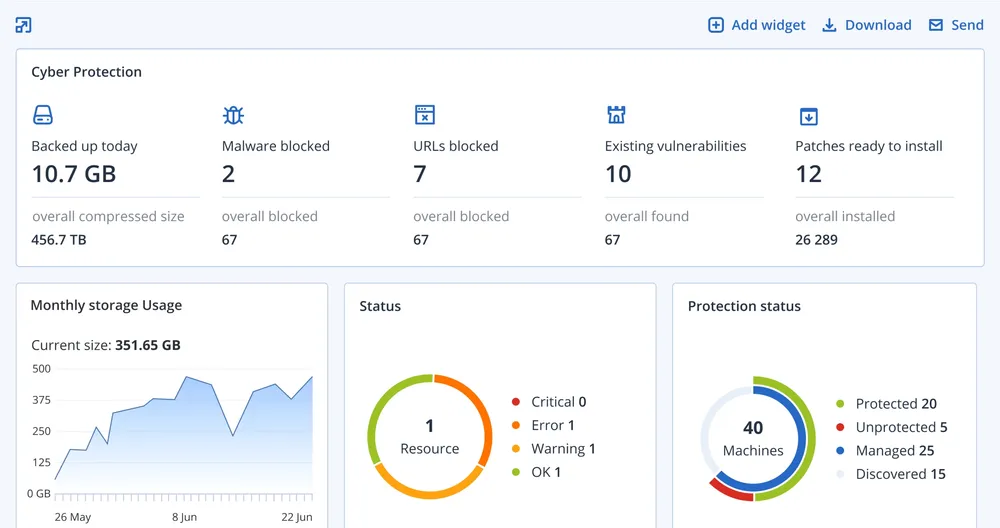
Advanced cyber resilience for every endpoint, across multi-site, mobile, and remote work environments.



Safeguarding multi-site and industrial IT against complexity, rising costs, and costly downtime.

Vulnerability assessments, patching, and malware removal from backups.

Continuous data protection with AI- and ML-driven real-time defence, blocking ransomware, zero-day threats, and other advanced malware.
Rapid data recovery with integrated disaster recovery and one-click, user-initiated restore, including bare-metal recovery.
See how Muttii Cyber Protect accelerates recovery, secures backups, reduces TCO, and strengthens multi-site and industrial IT against modern cyber threats.

Eliminates IT bottlenecks, reduces downtime, and saves time and money by empowering users to manage recovery.

Safeguards your data, applications, systems, and backups from ransomware, zero-day attacks, and other advanced malware.
Supports over 20 workloads across on-premises, cloud, and SaaS environments, with multi-generational OS compatibility, enabling vendor consolidation and full protection.

Minimises costly downtime on automated factory floors, in oil and gas operations, in pharmaceutical settings, and in air-gapped environments through rapid local recovery of OT, ICS, and scientific testing equipment

Provides a unified view of backup and recovery, offering centralised management and local autonomy. Offers seamless integration with existing third-party tools and extensive multi-generational OS support.

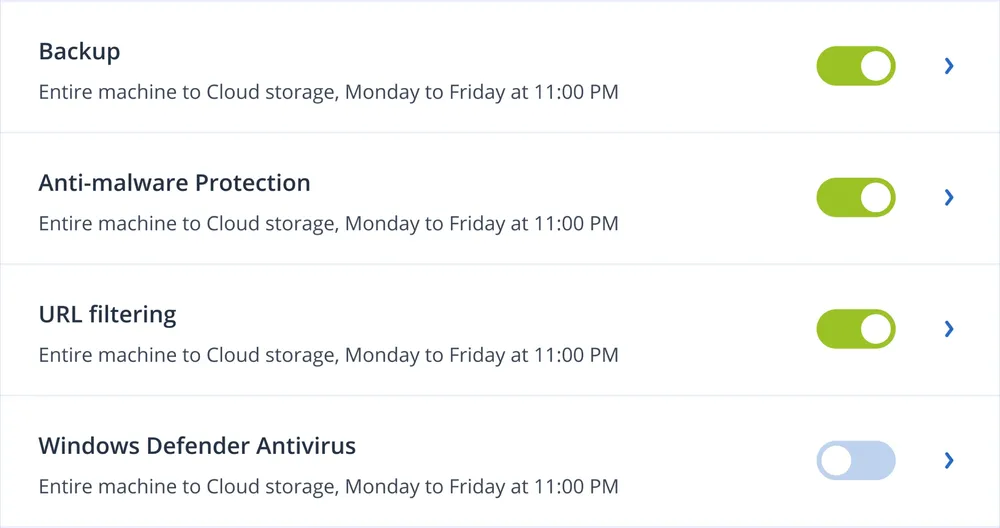
Protect new data as it’s created. Muttii’ agent monitors all changes in the specified applications and continuously backs them up, ensuring recent updates aren’t lost if the machine needs to be reimaged.


Store data in-house or leverage 54 global data centres, including Muttii Hosted, Google Cloud, and Microsoft Azure.

Enables self-service recovery of computers at remote sites and home offices, allowing operations to resume much faster without IT intervention.












AV-Test certified on macOS, Muttii achieved 100% malware detection with no false positives, protecting vast amounts of data.
Muttii ranked among just four solutions with zero false positives in the AV-Comparatives test.
Muttii all eight AV-TEST performance categories, Muttii achieved either a Very Fast or Fast rating.
Overview of Muttii Cyber Protect
Muttii Cyber Protect Licensing Overview
14 Questions to Assess Your Software Vendor Supply-Chain Risk
Windows PC
Mac

Muttii Cyber Protect v16 delivers rapid, user-driven recovery for any computing system, regardless of age or function—critical for minimising operational disruptions. Key features include:
Muttii Cyber Protect v16 is designed to quickly and efficiently restore systems online, with minimal technical involvement, making it ideal for demanding industrial settings.
Muttii Cyber Protect v16 helps lower the total cost of ownership (TCO) for cyber protection solutions through key features:
By combining these features, Muttii Cyber Protect v16 allows organisations to manage cyber protection efficiently and cost-effectively, lowering overall TCO.
Muttii Cyber Protect v16: Auto-Discovery
The auto-discovery feature simplifies safeguarding new devices across enterprise networks, particularly in multi-site and remote environments. Key benefits include:
In short, Muttii Cyber Protect v16’s auto-discovery streamlines network protection, delivers immediate and consistent security for new devices, and optimises IT resources.
Muttii Cloud Storage provides secure backup storage in Muttii Data Centers. Licenses are subscription-based and vary by storage capacity. You can back up an unlimited number of devices and platforms—including mobile devices—with the quota shared across all registered devices.*
Note: At least one Muttii Cyber Protect license is required to use Muttii Cloud Storage.
*Free cloud storage included with a subscription license applies only to the licensed workload and cannot be shared across other workloads.